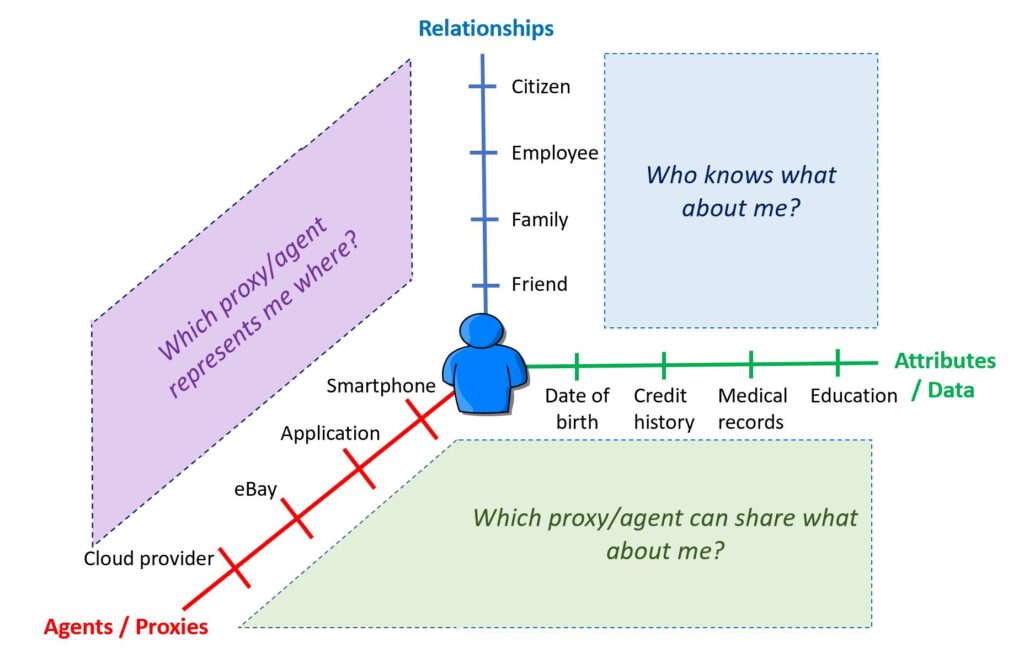
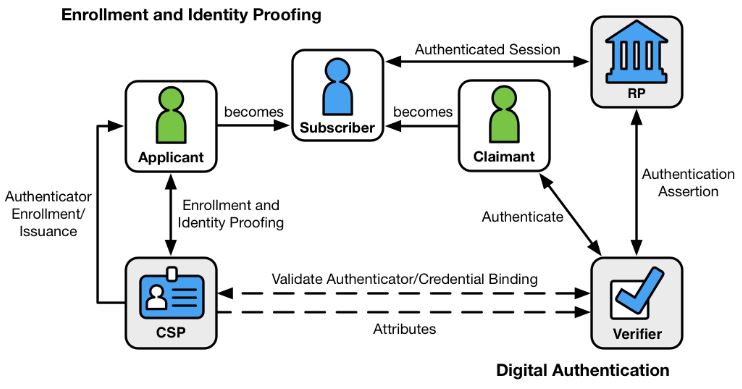
A couple of weeks ago Covid-19 prevented me from flying to Las Vegas for the Know Identity Conference and made me abandon my plan to write a post on what I discovered there.
So, having had a rethink over Easter, I decided to record my perception of the differences between Federated Identity and Self Sovereign Identity and why I think that Federation cannot provide the Internet’s missing identity layer.
Federated identity management (FIM) is a means to enable users to access the systems and applications of multiple organizations using one login credential. Identity federation allows users to maintain login credentials with multiple credential service providers (CSPs) (e.g., email or social media providers) and then choose among them when logging into different online services
NISTIR 8149
To my mind, the principal beneficiaries of federated identity are the business organisation (Identity Provider) not the citizen, through
- Increased efficiency and cost savings from not having to manage users’ login information;
- Improved risk management through multilateral agreements;
- Reduced privacy risks due to limited replication of users’ personal data across the organisation’s infrastructure;
- Improved system design criteria based on a defined risk profile that is aligned to the community being served.
But that is not to say that users of federated identity systems do not also derive some benefit, they clearly do:
- Improved user convenience and reduction in risk resulting from having fewer sets of usernames & passwords to remember and manage;
- Single Sign-On (SSO), enabled by FIM, is an efficient way for employees to access the corporate resources, applications and data they need to do their jobs.
- The organisation’s HR department and its associated access control mechanism act as a single source of the truth, preventing users from repeatedly entering personal details when requesting access to shared resources.
The downsides of Federation
But … what about us as Citizens, when we are not at work, when we are managing our online life and when we are using the Internet for our own personal reasons?
To operate effectively FIM needs multilateral and mutual trust between service providers, operating across a clearly identified infrastructure with an understood and consistent risk profile. For example the UK governments Verify solution relied on a common (and crucially) formally assessed risk profile for OFFICIAL information. Once an individual’s identity has been established by the identity providers operating Verify, that identity could be used by the citizen to gain access to various government services, such as benefits, taxes, driving licences, passports etc.
What’s good for the workplace doesn’t necessarily transfer to the wider world…
The Internet does not have the common risk profile and multilateral, mutual trust and governance that Federated Identity Management requires.
But not to worry, that yawning chasm is being filled by GAFAM, the Internet’s Big Five – Google, Apple, Facebook, Amazon and Microsoft!! Each time you come across one of these buttons, you are being offered the opportunity to share your identity with GAFAM.
So what’s wrong with that, you might ask.
Well lets have a look at the UK Information Commissioner’s 2018 Report to the UK Parliament on their investigation into the use of data analytics in political campaigns. Decide for yourself whether Facebook can be trusted with your identity data.
The ICO –
- Found found that between 2007 and 2014, Facebook processed the personal information of users unfairly by allowing application developers access to their information, without sufficiently clear and informed consent, and allowing access even if users had not downloaded the (personality testing) app, but were simply ‘friends’ of people who had. Facebook also failed to keep the personal information secure because it failed to make suitable checks on apps and developers using its platform
- Issued Facebook with the maximum monetary penalty of £500,000 available under the 1998 Data protection legislation.
- Referred Facebook to the Irish Data Protection Commission regarding their targeting functions and techniques used to
monitor individuals’ browsing habits, interactions and behaviour across the internet.
- Investigated other organisations linked to Facebook and engaged in buying and selling personal datasets in the UK, so called data brokers, were also subject to substantial monetary penalties.
- Concluded that Facebook did not take sufficient steps to prevent apps from collecting data in contravention of data protection law.
- Established that the personality test app utilised the Facebook login in order to request permission from the app user to access certain data from their Facebook accounts.
- Found that Facebook did not follow up on a request to Cambridge Analytica that personal data from Facebook be deleted
On the basis of evidence produced by the ICO I, for one, don’t trust the the privacy management capabilities of Facebook. I certainly won’t be trusting them with any more of my identity data and I’m disinclined to ask any of the Big 5 to act as arbiter of my identity.
There simply must be a better way of enabling single sign on to all manner of Internet services, including banking, medical records, online shopping, social networking, interaction with government services, holiday bookings, clubs and memberships, email, educational & professional qualifications, investments & mortgages etc… etc…
And there is…
Self Sovereign Identity
A number of leading lights in the SSI community have come together to write the definitive study of Self Sovereign Identity, which was published in May this year. I strongly the book because I believe it is an excellent and comprehensive source for all things SSI, VC and DI. It is essential reading for those interested in this intriguing and fast developing area of new technology.
Preukschat and Reed identify a number of reasons why the Federated Identity Model does NOT provide the missing Internet identity layer:
- There isn’t one IDP that works with all sites, services, and apps. So users need accounts with multiple IDPs, and pretty soon they start forgetting which IDP they used with which site, service, or app.
- Because they have to serve so many sites, IDPs must have “lowest common denominator” security and privacy policies.
- Many users—and many sites—are uncomfortable with having a “man in the middle” of all their relationships, particularly being able to surveil users login activity across multiple sites.
- Large IDPs represent some of the biggest honeypots for cybercrime ever created.
- IDP accounts are no more portable than separate accounts linked to each website (centralised model); if you leave an IDP like Facebook or Twitter, all those account logins are lost.
- Lastly, due the security and privacy concerns, IDPs are not in a position to help users securely share some of their most valuable personal data, e.g., passports, government identifiers, health data, financial data, etc.
The most important difference between SSI and FIM, though, is that SSI is no longer account-based. Instead there is a direct secure peer-to-peer relationship between the two parties i.e. a shared connection. Neither party “controls” the relationship and this is true whether the parties are people, organisations or things.
The key to the security of these connections is the underlying decentralized public key infrastructure (DPKI) that is supported by blockchain technology. Together these enable:
- The exchange of public keys directly between any two peers;
- The exchange of digital identity credentials (aka verifiable credentials) to provide proof of real world identity; and
- The storage of public keys on public blockchains specifically designed for the purpose.
In the centralized and federated identity models, the locus of control is with the issuers and verifiers in the network. In the decentralized self-sovereign identity models, the locus of control shifts to the individual identity owner, who can now interact as a full peer with everyone else.
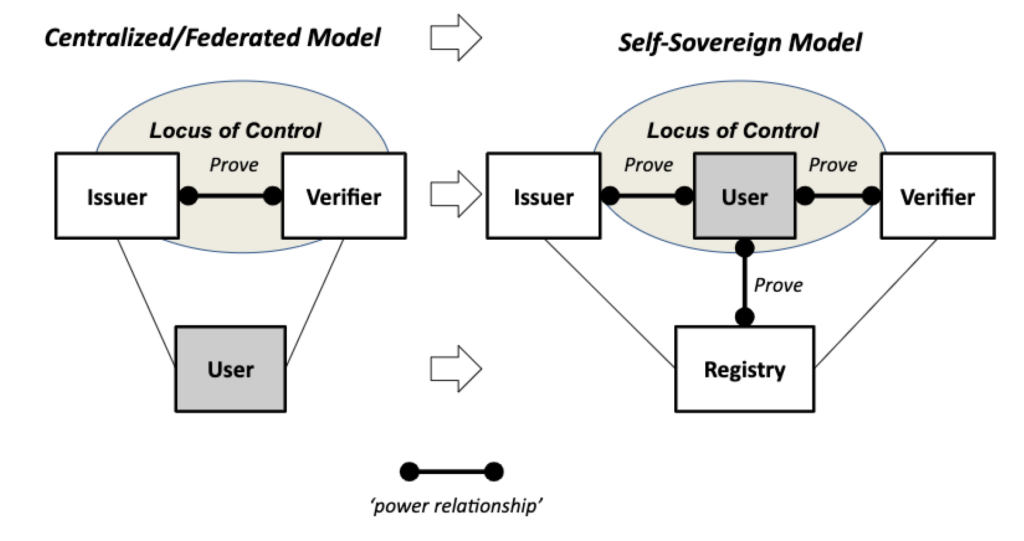
Preukschat and Reed summarise the differences between the FIM and SSI concepts of operation.
| FIM Architecture | The user first contacts the Service Provider, is then redirected to the Identity Provider where he/she logs in, and is then redirected back to the SP providing the latter with the user’s identity attributes that the IdP is willing to release. |
| SSI Architecture using VCs | There is none of this web-based redirection within a defined “federation”—the user as holder obtains VCs from issuers and uses them independently at any verifier that will accept them. |
Fundamentally, the SSI/VC philosophy is that users are paramount and it is only they that can decide who to present their VCs to, whilst the FIM philosophy is that IdPs are paramount and they decide who can receive the user’s identity attributes.
Today’s federated identity management infrastructures give issuers (IdPs) great power because they are at the centre of the ecosystem. SSI/VCs turn this model on its head and place users at the centre.
We started out trying to find a solution to the Internet’s missing identity layer; what we ended up discovering was that to solve those problems we needed a shift in control from the centres of the network—the many “powers that be”—to the edges of the network—where all of us exist and interact as peers.
Preukschat & Reed